Bitwarden - Product Vision and Problem Analysis
During the last year in the midst of a global pandemic, many companies were forced to bring their businesses online. Meetings, documents and whiteboards were all kept online so each employee could access these from their desk at home. Many of the applications that enable online collaboration require the employees to create an account. The application uses this as authorization to view the company’s confidential content. The application itself might have sophisticated security measures against cyber breaches, protecting the companies confidential information. But the need to create accounts is a risk unto itself. Employees often use weak or repetitive1,2 passwords, these form a weak link in the security of that information.
Creating strong unique passwords is hard enough as it is, remembering them for 10 or more different applications is even harder. It is, for this reason, Bitwarden offers a cross-platform, risk-free, and easy-to-use password manager. A password manager securely generates, remembers and saves all passwords of the user. The user chooses a strong master password that secures all this information. A strong password, e.g. “CY^4WA$W57EVWJ5doVvm” takes attackers centuries3 to crack. A weak password, e.g. “P@ssword” can be craked within minutes3. With open-source software behind all of the Bitwarden applications, the source code is certified not only through multiple professional companies but also by the users themselves. Bitwarden ensures all employees of a company follow secure protocol when it comes to password creation. It also enables safe file sharing, Single-Sign On authentication for enterprises, and, due to the open-source code, safe self-hosting options.
Key domain concepts
The Bitwarden system consists of multiple applications. Each part has its own distinct functionality or runs on a different platform. The main logic of the system is inside of the server application which is the backend of the system. This application includes the API, database, etc. The main logic is divided into, collections, events, groups, members, organizations, and policies. Each member is an entity that has a Bitwarden account and communicates via their client application with the API of the server application. The client application can be a browser extension, a desktop application, or a mobile app. The client application asks the user for their master password. By using the master password in combination with the login details of the user, the collection for passwords can be retrieved. The passwords are then locally decrypted to be used to login to other sites or applications. The vault of Bitwarden works in the same way.
Main use cases
In this section, a description of the system’s main capabilities (e.g. use cases), as they are visible to the typical end-user, will be given. As stated before, Bitwarden is a password manager. Its use cases can be divided into two groups, use cases for companies and use cases for individuals. Individuals mainly use Bitwarden to securely store and access their passwords at any time on any device. Individuals that have a paid plan can also safely encrypt e-mail attachments up to 1 GB. Besides employees of companies being able to access the use cases mentioned above, companies also use it for its password sharing and group management functionalities. This allows companies to easily and securely share passwords with employees that need them. Of course, individuals can also share passwords among a group.
Bitwardens main capabilities are4:
- Storing passwords securely, through the use of End-to-End Encryption
- Cross-Platform Accessibility: Access critical data in your Bitwarden vault from any location, browser, and device
- Secure Password Sharing: sharing encrypted data quickly and easily, and only with the users or teams who need access
Its secondary capabilities are4:
- Open-source software means it can be updated and improved by the Global Bitwarden Community
- Security Audit & Compliance: Open source and third-party audited, Bitwarden complies with Privacy Shield, GDPR5 and CCPA6 regulations
- Vault Health Reports: Access insightful reports to reveal weak, reused passwords, and other helpful data security metrics
- Directory Sync: A powerful Directory Connector streamlines user and group onboarding and keeps them in sync
- Detailed Event Logs: Bitwarden creates audit trails to help you keep track of user and group access to sensitive data
- Flexible Integrations: Unite existing systems with Bitwarden using Single Sign On authentication, Directory services, or powerful APIs
Context
The context in which Bitwarden operates is complex to such an extent that we can differentiate the business context from the technical context.
Bitwarden’s user-base ranges from individual users, who can use the free plan or pay for extra features, to families, teams and business organizations, that can choose between a free plan or multiple paid plans. There is even the option to self-host Bitwarden for businesses. For users to access Bitwarden they only need to input their email address and master password. This grants users access to their vault containing their username and password combinations for all other applications.
One of its biggest points of pride is that it supports cross-platform use. This means that Bitwarden has to deal with iOS, Android, Windows, MacOS, and Linux as operating systems and the web for online use, which in turn leads to the use of Electron for its desktop application, Xamarin for the mobile app, and Angular for its web vault and browser extensions. These are all front-end development frameworks. A client-side application is not all that is needed for this service, as the user data has to be stored in a database and this data needs to be retrieved and shown in the client-side applications. All of these back-end functionalities are bundled into the server containing an API, an admin module, a billing module, a relational database, and more. This entire infrastructure uses managed cloud services 7. Content from the database can be managed through the Bitwarden Public API.
Stakeholders

Figure: Bitwarden stakeholders
The Bitwarden project has multiple stakeholders. Below we will discuss the main ones: Bitwarden company, private- and enterprise customers.
The Bitwarden company is the main stakeholder in the Bitwarden project. They are the main contributors to the project and they review all-new features, bugs and manage the road map of all the projects. The Bitwarden company takes this road map upon itself as the link between the enterprise customers and new features. The project is open-source, so is the forum where discussions are held and the issue list. Although this is speculative, we can imagine enterprise customers can have feature requests they might like to offer anonymously. Besides that, enterprise customers are the highest paying customers, meaning their feature requests can have priority over feature requests from freemium users. The Bitwarden company is the shareholder that manages these things.
Besides the company, there are also the users or customers of Bitwarden. There are two sorts of customers, the first are private customers. These individuals or families can make use of a free plan, or pay a monthly fee for premium features. These users want to use Bitwarden as a safe application to store passwords. Some of them will be interested in providing feedback, testing experimental features as well requesting features, and offering bug reports to the project. Besides the developers offered by the Bitwarden company, we expect that open source contributors would also privately use Bitwarden, such as ourselves.
Finally, we also have enterprise customers. These companies hire Bitwarden for a fee to not only offer their employees the password manager but to safely store and access files from the cloud. Self-hosting an instance can be very worthwhile for many companies as the open-source nature of the code does not incur any risks of code being stolen. Besides that this ensures the company can uphold a rigorous security protocol in regards to log-in and password requirements. Executing this protocol is made easy through the Bitwarden application.
Key Quality Attributes
Availability
The hosting of the collections of passwords of each user is done by Bitwarden itself.
This means that when a user wants to use the synchronization option between devices, meaning that the user can use its passwords on all of their devices, the hosting should be available.
This could lead to an issue in regards to the availability of hosting.
Namely, when the servers of Bitwarden aren’t available for a while, the new passwords created by the users aren’t saved to the cloud, which can result in loss of passwords when the locally saved data of the user is corrupted by, for example, a failing hard drive of the user’s computer.
Security
Servers of Bitwarden themselves need to be secure, as sensitive data is stored on those servers.
Luckily, if all the protocols of Bitwarden are correctly used, all the sensitive data on the servers are encrypted.
The End-to-End encryption makes sure that all data is encrypted before is it sent. 8
Only the master password of the user or company can decrypt the vault contains the passwords and documents.
The master password is on itself only stored in an encrypted form on the cloud of Bitwarden as well.
This way Bitwarden doesn’t have access to the content of the vault.
When one loses or forgets its master password, however, the vault is no longer accessible.
This is what Bitwarden calls the Zero Knowledge architecture.9
This architecture can be seen in Figure 10.
Figure:
Bitwarden zero knowledge encryption architecture

Transparency By being an open-source project Bitwarden believes it contributes to a high standard of security. ‘We believe source code transparency should be a requirement for online security solutions like ours’ 4. By being open-source, the community can help to find bugs or prevent new ones.11 The transparency of the system also helps to remove any doubts people might have about sharing their sensitive data with a company. Everyone can see exactly how the data is used. At last, the system is audited by a 3rd party as well. The security experts of Cure53 check the system and analyze the cryptography used.12
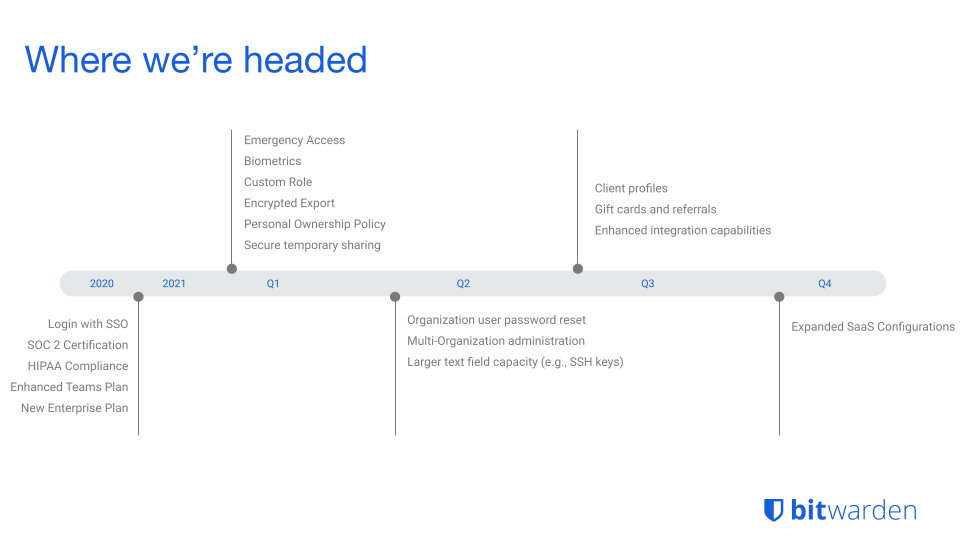
Product Roadmap
This section will discuss the planned updates for Bitwarden. Since Bitwarden is owned by a company, an official roadmap is available. It has been published by the Bitwarden company on their website. While the open-source contributors can make suggestions for the future development of Bitwarden, it is the company that has the final say about what features get added or not. The Bitwarden company states: “Items are picked with a compromise of what the community forums are asking for, what our enterprise customers need and want, and items that Bitwarden wishes to implement based on our product strategy.”13 Bitwarden recognizes that while most times the items picked will overlap with the highest community votes, sometimes they may not.
A visual representation13 of the biggest planned changes can be seen below:
Figure:
Bitwarden 2021 roadmap
Ethical considerations
Bitwarden, as a password managing application, is inherently vulnerable to privacy and security issues. Since it’s main selling point is that it enables far greater security by enabling users to have unique randomized passwords for each service, it is at least far more secure than not using its service. With an application managing, storing, and sharing highly sensitive information it is always a concern how this company handles its data and the product is only as secure as its willingness to keep to its ethical beliefs. Bitwarden makes a strong ethical case by being completely transparent in their codebase by making it open-source 14. This helps them gain the trust of the public in both privacy and security, in contrast to big tech firms as Google and Facebook, who are infamous for their shady practices on these topics 15,16. The open-source project provides everyone the opportunity to double-check the developers. It prioritizes secure practices over the ability to recover your account when the master password is lost as Bitwarden has no knowledge of, no way to retrieve, and no way to reset it 17. This feature indicates how serious Bitwarden is about security. Another security-focused practice is that all passwords are first encrypted before it is sent to its servers, where the soundness of this approach can be inspected by everyone who pleases. Despite the enormous benefits provided, it is important to mention that open-source software has a downside. It is possible for malicious users to find vulnerabilities in the source code that is available online and abuse these weaknesses. Although this is a real threat, the improved security and privacy due to open-sourcing greatly outweigh the potential threat.
-
Bowen, K. (2020, June 30). Your Employees Are Reusing Passwords – Find Out How Many. Infosecurity Magazine. https://www.infosecurity-magazine.com/blogs/your-employees-reusing-passwords/#:%7E:text=As%20many%20as%2065%25%20of,by%20Google%20%E2%80%93%20and%20it’s%20understandable. ↩︎
-
Poll, H. (2018, December). Online security survey [Infographic]. Services.Google.Com. https://services.google.com/fh/files/blogs/google_security_infographic.pdf ↩︎
-
zxcvbn. (n.d.). Password strength tests (zxcvbn). Github.Io. Retrieved March 29, 2021, from https://lowe.github.io/tryzxcvbn/ ↩︎
-
Bitwarden. (n.d.). Product Page. Bitwarden.Com. Retrieved March 8, 2021, from https://bitwarden.com/products/ ↩︎
-
General Data Protection Regulation. (2018, May 25). GDPR Info. https://gdpr-info.eu/ ↩︎
-
California Consumer Privacy Act (CCPA). (n.d.). State of California Department of Justice. Retrieved March 8, 2021, from https://oag.ca.gov/privacy/ccpa ↩︎
-
Nesbitt, S. (2018, March 19). Behind the scenes with the Bitwarden password manager. Opensource.Com. https://opensource.com/article/18/3/behind-scenes-bitwarden ↩︎
-
Orenstein, G. (2020, June 13). Vault Security in the Bitwarden Password Manager. Bitwarden Blog. https://bitwarden.com/blog/post/vault-security-bitwarden-password-manager ↩︎
-
Orenstein, G. (2020b, August 6). How End-to-End Encryption Paves the Way for Zero Knowledge. Bitwarden Blog. https://bitwarden.com/blog/post/end-to-end-encryption-and-zero-knowledge/ ↩︎
-
Spearrin, K., Marshal, A., & Orenstein, G. (2020, August 20). Building a zero knowledge architecture[Slides]. Crowdcast. https://www.crowdcast.io/e/zero-knowledge-architecture ↩︎
-
Bitwarden Hackerone. (2017, July 1). Bitwarden Hackerone. https://hackerone.com/bitwarden?type=team ↩︎
-
Spearrin, K. (2020, June 22). Bitwarden 2020 Security Audit is Complete. Bitwarden Blog. https://bitwarden.com/blog/post/bitwarden-network-security-assessment-2020/ ↩︎
-
Greer, T. & Bitwarden. (2021, February 26). Bitwarden Roadmap. Bitwarden Community Forums. https://community.bitwarden.com/t/bitwarden-roadmap/12865 ↩︎
-
Mercuri, R. T. (2005). Trusting in transparency. Communications of the ACM, 48(5), 15–19. https://doi.org/10.1145/1060710.1060726 ↩︎
-
Confessore, N. (2018, November 15). Cambridge Analytica and Facebook: The Scandal and the Fallout So Far. The New York Times. https://www.nytimes.com/2018/04/04/us/politics/cambridge-analytica-scandal-fallout.html ↩︎
-
MacMillan, D., & McMillan, R. (2018, October 8). Google Exposed User Data, Feared Repercussions of Disclosing to Public. WSJ. https://www.wsj.com/articles/google-exposed-user-data-feared-repercussions-of-disclosing-to-public-1539017194 ↩︎
-
Bitwarden. (n.d.). I Forgot my Master Password. Bitwarden.Com. Retrieved March 8, 2021, from https://bitwarden.com/help/article/forgot-master-password/ ↩︎